The massive cyber attacks on March 20 that paralyzed the computer systems of South Korea’s three major TV broadcasters such as KBS, MBC and YTN, and major banks such as Shinhan Bank and Nonghyup have terrified the whole nation. And who’s behind the attacks has finally come to light.
Amid rumor and speculations running rampant surrounding who’s responsible for the attacks, Issuemakerslab has discovered that the March 20th cyber attacks were carried out by a hacker group who has actually been staging cyber warfare with South Korea since 2007 stealing data and information from the nation--some are confidential.
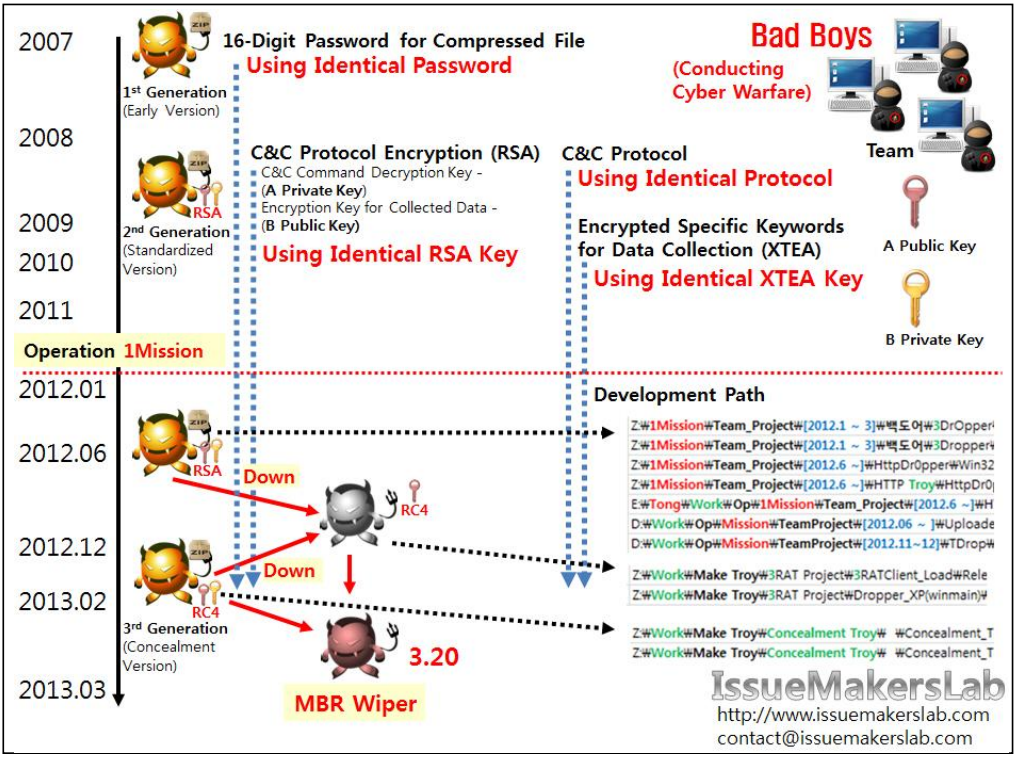
Figure 1. Evidence that shows the hacker group that has been staging cyber warfare for the past 6 years is identical with the group that attacked South Korea on March 20 (Source: IssueMakersLab)
Most notably, the attacks had been meticulously planned by the hacker group since early 2012 under the name of ‘Operation IMission1.
‘IssueMakersLab’ has confirmed based on the evidence they gathered that a hacker group they have been tracking down for the past 6 years is the same one that attacked South Korea on March 20th.
| Evidence List | Contents | Remarks |
|---|---|---|
| Using Identical 16-Digit Password for File Compression | Identical password was used for compressing the list of filenames collected. | Identical 16-Digit Password for Compression (including Upper 公L Lower Case Letter/Number/Special Character) |
| Identical Stage 1 C&C Protocol | Using Identical Command Control Code Identical File Name Created When Receiving Command Identical File Name Used When Sending Data Identical 2 RSA Key Pairs Used for C&C Protocol Encryption -C&C Command Decryption Key (A Private Key) -Encryption Key for Collected Data (B Public Key) | RSA Keys Owned by Hacker -C&C Command Encryption Key (A Public Key, pair of A Private Key) -Decryption Key for Collected Data (B Private Key, pair of B Public Key) Only the Hackers Own B Private Key to Decrypt Collected Data. (Note, some versions started to use RC4 stream encryption from late 2012.) |
| Identical Certain Collection Keyword & Encryption Key | Identical Key Used to Encrypt Keywords to Collect Secrete National Intelligence | Using XTEA Encryption Algorithm |
| Development Path | Development Path Used for Team Projects within One Hacker Group | Development Path Includes Korean Words such as '백도어' (Backdoor in English), '작전준비, (Operation Preparation in English) and '우히’ (Bypass in English). |
Table 1. Evidence that shows the hacker group that has been staging cyber warfare for the past 6 years
is identical with the group that attacked South Korea on March 20 (Source: IssueMakersLab)
The table above shows that the malwares that have been used for the past 6 years have been produced by one specific hacker group. C&C protocols that have been used for the past 6 years by the hacker group such as passwords used
when compressing the list of the files to collect and control codes used to control commands are identical with the ones used for the March 20th attacks.
In particular, the hacker group used RSA encryption algorithm for communication and the same public key has been used for the past 6 years. The malware used public key to encrypt the collected data and only the hackers who have private key can decrypt them.
In addition, the same key was used for encrypting keywords for secret national intelligence and, the development path shows high level of similarity. There seems to be a few teams within the same hacker group to develop malwares.
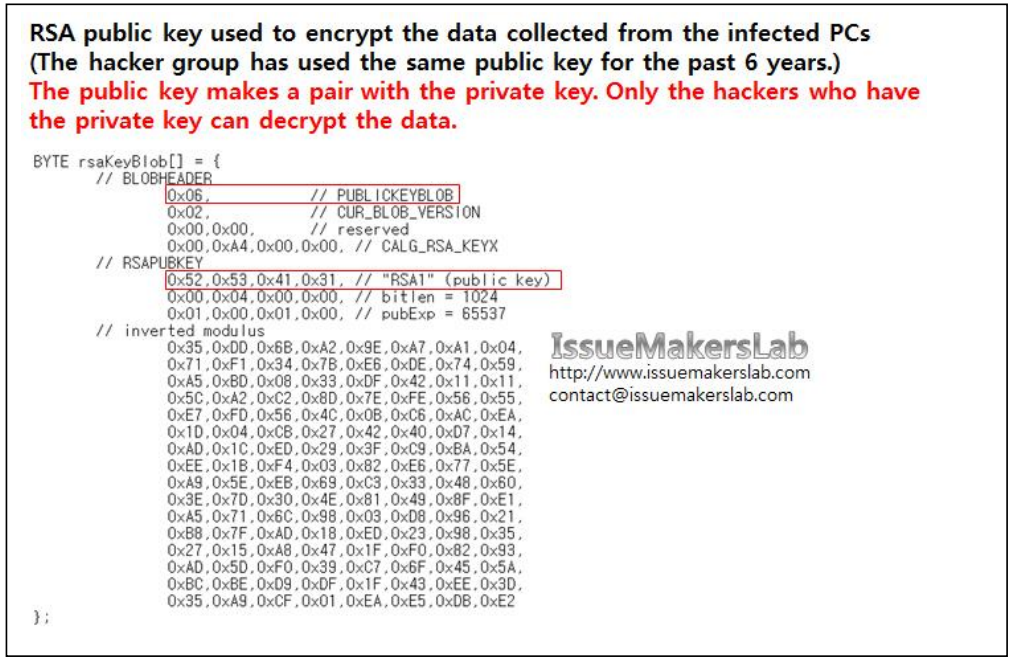
Figure 2. The hacker group has used the same RSA key for the past 6 years. (Source: IssueMakersLab)
More alarming is that the hacker group has been conducting a campaign of cyber attacks targeting South Korea for the past 6 years aiming to steal the nation’s secret information. They used Korean keywords such as ‘키리졸브 (meaning Key Resolve in English)’, ‘작전 (meaning operation in English) and ‘미군 (meaning US Army in English)’, and English keywords such as ‘Key Resolve’ and ‘Warfare’.
According to IssueMakersLab, the hackers have stored encrypted keywords of the information they want to capture in malwares and collected the files with the titles that include the keywords.
In preparation for the March 20th cyber terror, the hackers had circulated malwares without keywords to the affected broadcasters and banks and, at the same time, some malwares that contain keywords to other critical institutes in South Korea. The malwares that contain the keywords below were already circulated in South Korea early 2010.
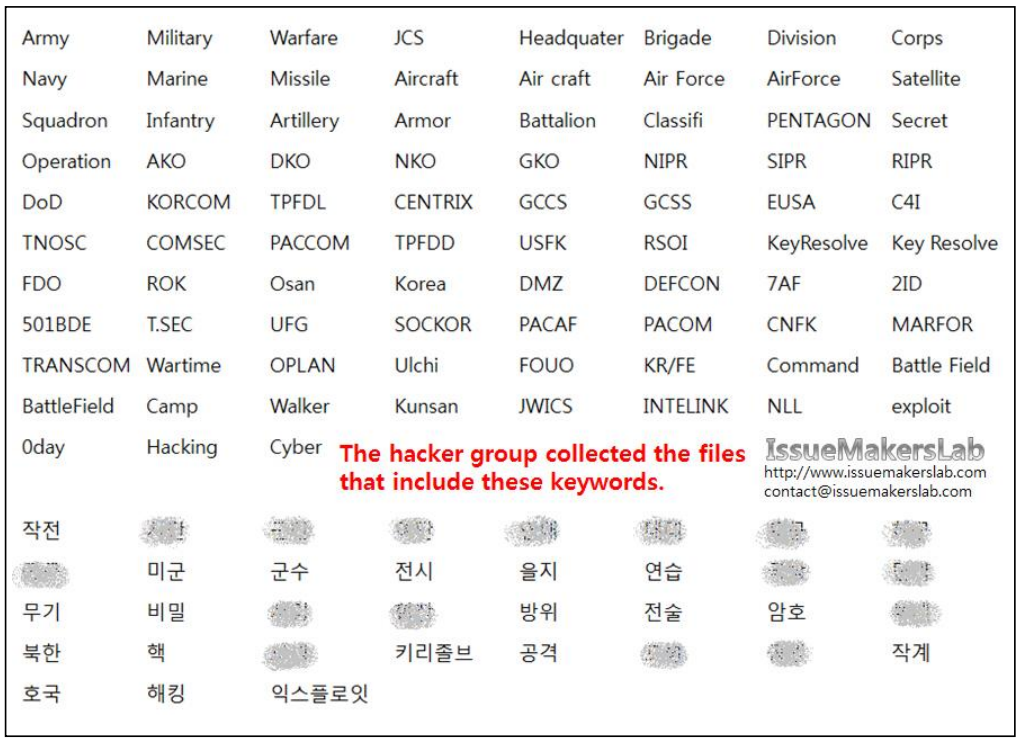
Figure 3. The above keywords were included in the files the hackers collected. (Source: IssueMakersLab)